Today I found some time to sit down and figure out why my ASA box was denying ping, traceroute and other ICMP traffic. Denying all ICMP traffic is the most secure option, and I think Cisco made a good choice by making this the default. However, I really wanted to be able to ping and traceroute from inside my network to the outside world, if for no other reason than to check the latency of my servers. Here’s how to do it in ASDM.
The address on the outside interface that we are trying to ping is assigned via DHCP. Below is the running config. We are using Easy VPN to establish a VPN connection back to our office. ASA Version 8.2(2)! Hostname ASA5505. Enable password encrypted. Passwd encrypted. Interface Vlan1. Security-level 100.
- The ASDM image can be downloaded on Cisco's website by going to: Downloads Home Products Security Firewalls Firewall Management Adaptive Security Device Manager. Ciscoasa# ping 192.168.1.3 // PING TO TFTP SERVER.
- I have a Cisco ASA 5510 inherited from a predessor, running ASDM 6.2 It apparently does not allow pings to either the DMZ or outside world by policy. I looked in the Firewall-Polcy- Inspect Maps, there are a number of protocols, i.e. FTP, HTTP, SCCP, SIP, etc, but not ICMP. Is it not possible to enable ICMP inspect via the ASDM interface?
- When you first setting up a Cisco ASA firewall, one of the most common requirements is to allow internal hosts to be able to ping the Internet. It is not only for the convenience that a network administrator to check if the Internet is up by pinging Google.com, but also for certain applications to work.

Install Asdm Cisco Asa
Cisco Asa Allow Ping Asdm
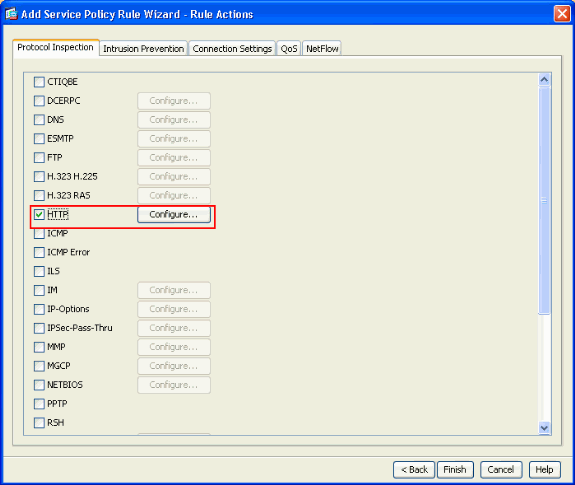
First, open an ASDM connection to your router. Go into the Configuration screens and click on Firewall to configure the firewall options. Then click on Service Policy Rules to configure the services that the firewall software will monitor. Select the global policy (first and only one in the list), and click on the Edit button. Switch to the Rule Actions (3rd) tab, and in the list check to enable ICMP. You can leave ICMP Error unchecked. Close that and Apply the changes.
Now, if you just want to be able to ping, stop here and you are done. However, traceroute will not work with this setup. For traceroute to work, you have to complete this follow-up task.
Asa Asdm Setup
While still under the Firewall configuration switch to the Access Rules item. Add an access rule to permit ICMP traffic. Click the Add button, make sure the interface is set to outside, action is Permit, and Source/Destination is any. Under Service, click the … button and select the icmp line and click OK. Click OK again in the Add Access Rule dialog and Apply the results to finish the process.




